About us
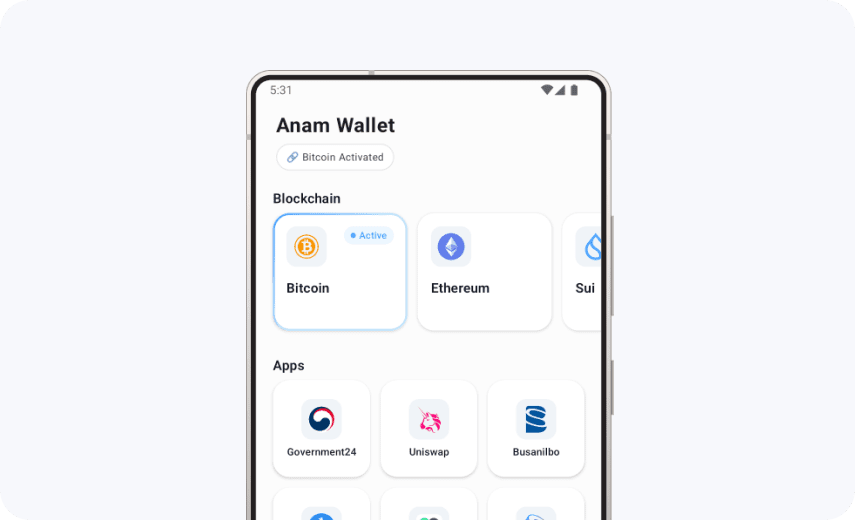
Introducing AnamWallet
Opening Infinite Possibilities
with Modular Wallet
Currently, most cryptocurrency wallets have an inconvenient
monolithic structure with structural problems.
To solve these problems, we propose the world's first
security-focused modular cryptocurrency wallet
considering dynamic expansion, isolated security, and user convenience.


2025
01
Participation in CES 2025 (Korea University Pavilion)
05
Establishment of Corporate Research Institute
09
Official Launch of Busan Wallet (Scheduled)
2024
04
Signed ABKO Research Institute Management Contract
(5 years, 900 million KRW)
08
Selected for KTSEP Startup Growth Technology Development Project Stepping Stone Growth Network R&D
(1 year, 120 million KRW)
2023 하반기
12
Signed ABKO CTO Advisory Contract
(3 years, 360 million KRW)
2023 상반기
03
Established Anam145
04
Selected for Pre-Startup Package
Selected for Tokamak GrantTON
Professor Junghee Lee, Ph.D.(CEO)

Dr. Junghee Lee is a world-renowned scholar and industry leader in cybersecurity and blockchain technology. He earned his Ph.D. in Engineering from the Georgia Institute of Technology (Georgia Tech, USA) and currently serves as a Full Professor of Cybersecurity at Korea University, often referred to as the "Ivy League of Korea."
Professor Lee has published numerous papers in SCI top-tier journals, establishing himself as a global authority in information security. Beyond academia, he co-founded Anam145, a leading blockchain and cybersecurity company, which is now delivering next-generation modular blockchain wallets for South Korea's second-largest city, Busan.
His unique expertise—bridging deep academic research with real-world blockchain infrastructure—positions him at the forefront of building secure, transparent, and scalable digital financial systems for both Korea and international partners.
Key Publications
MultiFile View: File-view-based Isolation in a Single-User Environment to Protect User Data Files
Isolation technology is often used to reduce the impact of cyber attacks, and it is mainly used in multi-user environments. Representative examples of said technology include access-control mechanisms and virtual machines. In a single-user environment, virtual addressing and a trusted execution environment isolate applications. However, the focus of such techniques is usually only on isolation, while the sharing of files has not been given much attention. In a single-user environment, users have the ability to access the same file through multiple applications. In this paper, we introduce the concept of file view, and propose file isolation based on the notion of views. Under the proposed MultiFile View mechanism, files within a view can be accessed by multiple applications when that particular view is activated. In other words, files appear only if their associated view is activated. The proposed technique is effective in protecting files from attacks on user data files, such as ransomware, wiper, and evil maid attacks. We also develop three models to describe how to assign views to applications. The proposed technique is prototyped in Windows 10. Through extensive experiments, we demonstrate that the new technique’s performance overhead does not noticeably affect the overall user experience.
PhantomFS: File-Based Deception Technology for Thwarting Malicious Users
File-based deception technologies can be used as an additional security barrier when adversaries have successfully gained access to a host evading intrusion detection systems. Adversaries are detected if they access fake files. Though previous works have mainly focused on using user data files as decoys, this concept can be applied to system files. If so, it is expected to be effective in detecting malicious users because it is very difficult to commit an attack without accessing a single system file. However, it may suffer from excessive false alarms by legitimate system services such as file indexing and searching. Legitimate users may also access fake files by mistake. This paper addresses this issue by introducing a hidden interface. Legitimate users and applications access files through the hidden interface which does not show fake files. The hidden interface can also be utilized to hide sensitive files by hiding them from the regular interface. By experiments, we demonstrate the proposed technique incurs negligible performance overhead, and it is an effective countermeasure to various attack scenarios and practical in that it does not generate false alarms for legitimate applications and users.
CryptoPad: Dedicated Device for Convenient and Secure Wallet
Abstract—As attacks against cryptocurrencies, such as stealing private keys or executing fraudulent transactions to transfer users' assets to attackers' addresses, increase, so does the significance of wallet security. There has always been a trade-off between convenience and security of various types of wallets. In this paper, we present CryptoPad, a dedicated device wallet, to address this issue. CryptoPad is a device where only pre-installed apps can run. CryptoPad is as convenient as a software wallet because a regular software wallet is installed on it. At the same time, we show that it is as secure as a hardware wallet through threat analysis.
DISKSHIELD: A Data Tamper-Resistant Storage for Intel SGX
With the increasing importance of data, the threat of malware which destroys data has been increasing. If malware acquires the highest software privilege, any attempt to detect and remove malware can be disabled. In this paper, we propose DISKSHIELD, a secure storage framework. DISKSHIELD uses Intel SGX to provide Trusted Execution Environment (TEE) to the host, implements the file system into SSD firmware that provides a Trusted Computing Base (TCB), and uses a two-way authentication mechanism to securely transfer data from the host TEE to the SSD TCB against data tampering attacks. This design frees DISKSHIELD from attacks to the kernel. To show the efficacy of DISKSHIELD, we prototyped a DISKSHIELD system by modifying Intel IPFS and developing a device file system on the Jasmine OpenSSD Platform in a Linux environment. Our results show that DISKSHIELD provides strong data tamper resistance the throughput of read and write is on average to 28%, 19% lower than IPFS.
Development of a secure and multi-blockchain enabled cryptocurrency wallet
Currently, most cryptocurrency wallets that can securely manage digital assets on blockchain networks only support a specific blockchain network. When developing a wallet that supports multiple blockchain networks, security vulnerabilities caused by a specific network are bound to spread to the entire system unless each network is separated at the system level. In this paper, we propose a cryptocurrency wallet solution that can support multiple blockchain networks simultaneously. To support multiple blockchain networks, the system is modularized by designing each module process responsible for cryptocurrency transactions to support different blockchain networks. Each module process and the functional blocks within the cryptocurrency wallet are independent processes, so even if a particular module is attacked, other functional blocks and module processes occupy independent virtual address spaces, which shows improved security. In our experiments, the cryptocurrency processing speed overhead caused by the multi-process structure is very small, around 8%.
